Open the world of Blockchain development - Chapter 3: Understand the math inside Cryptography
Being a store of worth thing meaning it must be strong to protect itself. This chapter we will get close to cryptography. The way they deal with sensitive information, and still keeping it public that everyone can verify it. Let’s go!
How you can keep the secret
On Blockchain or any other field that uses Cryptography or can be called Digital Signatures, there are two types of keys that go together, that is Private key and Public key.
Before Cryptography, we usually using fingerprint or written signature because we know only that person can make it (although it could be fake). In digital world, it still the same. If a message have a signature that you know it’s Public key. You know the person created that without knowing the value of their Private key.
More than it, the scenario addition that you can send a secret message to owner of Public key by using that key to encrypt your message, then only it’s owner can decrypt and read that message.
It like Alice using Bob locker to lock her message on the box then send it to Bob. Then Box using his key to unlock that box and read message inside, no one else can read that message even Alice but why do she need it?
Go deeper
Let’s talk about a little bit about mathematical, the cryptography that stand behind of the mechanism above is Elliptic Curve Cryptography (ECC). It is a way of one-way math problem, easy to solve it one way, the other way is intractable. For example if you have a question about how 23144*12343, the answer will be easy one on calculator, it is 285666392. Then how to you revert from 285666392 to 23144 multiply by 12343? Impossible, right.
ECC is not working exactly like that, for the easy one we could use the form:
y2 = x3 + ax + b
This formula mean a straight line can only catch the curve line at most 3 point. We have P point then Q point on the line of curve, you will have R point like this:

Then you drop R to other side of curve line to have R’ like this:

Now we connect two point P and R’, it will create another straight line that can cross will curve line in new point that called S, then make S’ and loop it over and over again then stop at a number of unknown time.
We have P . Q -> R then P . R’ -> S then over and over again.
In this case we have P as public one n time of dot is private one so it will be challenge to find Q point if you only know the result.
And of cause, this formula has some limit time if it cause on special case.

Finally, to make sure it secure, here is it secure level if you want to know:

Back to the Blockchain, where is it?
Based on HD wallet architect, there are many wallet follow this rule:
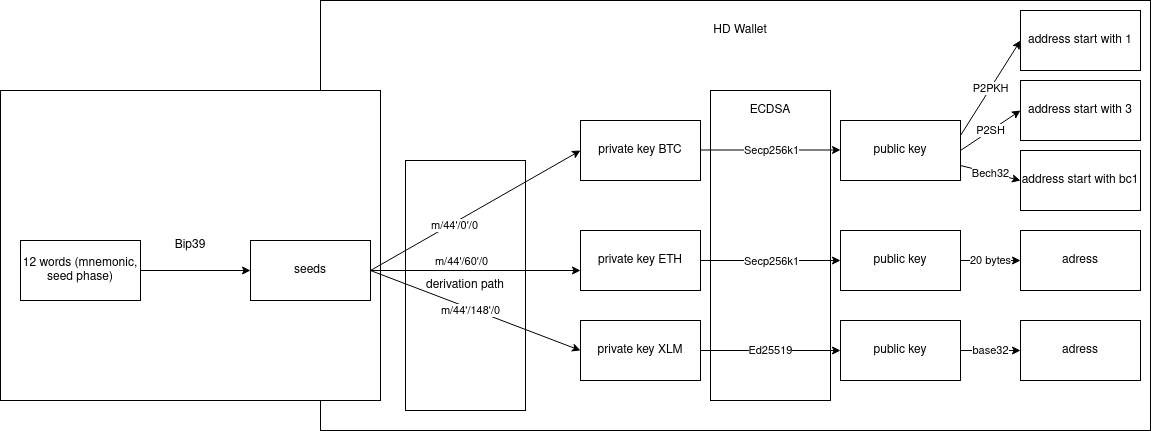
Here it is, can you see ECDSA? It stand for Elliptic Curve Digital Signature Algorithm and that is where we are using ECC.
Okay, let’s explain this diagram:
- Before going to the HD wallet phase there a part that we beginning, start with 12 words called mnenonic or seed phase, by using bip39 algorithm we make it into 32 bytes seeds.
- Then, that 32 bytes seeds going through a derivation path depend on that type of token like m/44’/0’/0 for Bitcoin or m/44’/60’/0 for Ethereum and then we have the result as a Private key.
- Private key using ECDSA like Secp256k1, ED25519, … to calculator Public key.
- Then Public key just using some more unique way depend on each type of Blockchain to make address more specific for it. Of cause if a signature create by Private key, it still have Public key inside to verify with address using to executed.